For both home and organizational networks, the public sectors of the Internet provide means for benefiting productivity and means of reaching for information when needed. However, Internet access allows enables the “outside world” to interact with the same local/public network assets which can open the doors to most modern day cyber-threats. Through this article, I will discuss the importance of a firewall as well as diving into the differences between a hardware firewall vs software firewall.
What is the Main Purpose of a Firewall?
In general, a firewall is considered a cost-effective way to work as a style of “perimeter security” to provide both protection of Internet-based attacks as well as create a choke point where data security is incorporated.
The other purpose a firewall gives is an additional layer of defense to support other countermeasures like within anti-virus/anti-malware and what is defined within the access control lists found in packet filtering to allow or deny traffic.
Characteristics of Firewalls
In general, all inbound (ingress) and outbound (egress) traffic must pass through the firewall with only authorized traffic as defined by the local security policy found on a local network would be allowed to pass through the firewall…think of how a 4-way traffic light works and you would be able to understand how a firewall works in the same way.
The examples of traffic that could be seen passing through the firewall is dependent of IP address ranges, protocols (along with the ports they serve), software programs, and trusted content types (this can be web server type content to file types).
Another general characteristic of a firewall is that it is less likely of being penetrated when in use of a hardened system within a patched and trusted operating system.
Most firewalls can be setup from a single, solo computer found within your home network to more complex situations where 2 or more systems are running in cooperation to perform and support the firewall functionality.
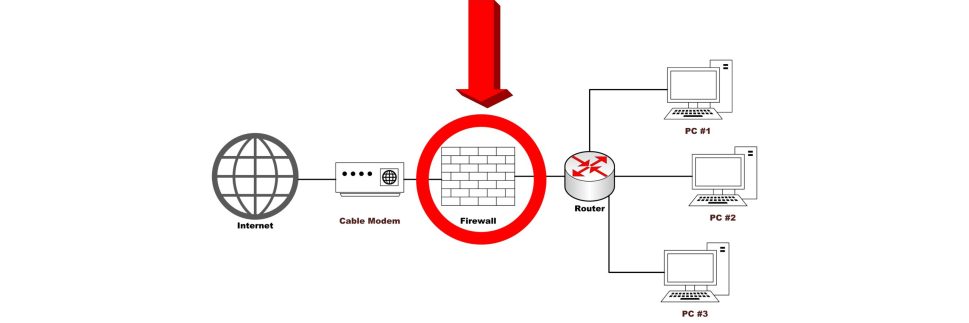
Firewalls are inserted between the premises of the network and the Internet to establish a controllable link in which to setup an outer security perimeter to separate the public Internet and the private sectors of each individuals local area network.
Used with IPSec and IKEv2, a firewall can control access based on the users identity especially for users who would use two-factor authentication to allow the user and their local traffic to be allowed through the firewall. This can be seen through a Virtual Private Network that uses these protocols.
Lastly, firewalls protect a network segment called a DMZ network or demilitarized zone network that is located between the external and internal firewalls where different servers are made to be externally accessed; but, also need monitoring. These servers can include a DNS, E-Mail, or a VOIP server that require two-way protection.
Types of Firewalls
There are many ways a firewall can be implemented both on the internal and external network to monitor network traffic individually from the small home network to a larger traffic flow in an enterprise with more than a 100 users.
There are only 2 types of firewalls that can be used in both environments: a hardware firewall or a software firewall
Software Firewalls

Beginning with the most common firewall and considered one of the easiest firewalls to maintain for a beginner or non-techie, a software firewall is what is seen as an integrated solution with Windows Defender or within a 3rd party anti-virus such as Avast and Bitdefender.
A software firewall is also considered a “host-based firewall” where it is used on both the Windows 10 and Mac OS X platform today. This type of firewall can be used to block unused ports on an endpoint device as well as white-list/black-list inbound traffic.
Beneficial for its simplicity, a software firewall would simply list applications to allow or deny as they are placed on a user’s computer rather than what is seen on a network firewall (this is a hardware firewall…which will be touched on in the below section) where there are more rule sets to be defined.
From a corporate setting, host-based firewalls can implement security policies as defined in most Windows and Linux servers with the filtering differentiating with different applications used by each end-host on the network.
In conjunction to how host-based firewalls are configured, the same policies already configured would automatically be synced to any new server added to the network even if the new server has its own firewall meaning there is no need to modify the network firewall configuration in order for the existing host-based firewall to work (in lament terms, the software firewall takes priority and placement of the integrated firewall already on the server).
Hardware Firewalls

Pictured above is the TP-Link AC1900 Router which has an integrated SPI firewall.
Considered a much more “advanced” configured firewall to maintain, a hardware firewall appliance is housed today in most modern routers (like the to connect to either a cable or DSL modem.
Hardware firewalls can be considered a “personal firewall” where they would simply block any unauthorized remote access to any connected computers on the LAN while monitoring anomaly activity in an attempt to block common malware (worms, viruses, DDoS, etc.).
Getting back to firewall integration within home routers, the type of firewall found within these routers are known as Stateful Packet Inspection (SPI) firewalls that raises the bar against a traditional packet filtering firewall.
SPI hardware firewalls amps up the rules for TCP traffic by creating a directory of all outbound TCP traffic and establishing each TCP connection in a table.
By performing this, SPI firewalls uses a packet filter to allow incoming traffic to open ports only for the packets that fit the profile of one of the entries in the directory table.
SPI firewalls keep track of TPC sequence numbers to prevent attacks as seen in session hijacking and maintain proper inspection of all data from protocols in file-transfer protocol (FTP), domain name server (DNS), simple network management protocol (SNMP), and more that generate high traffic volumes in real-time.
For corporate environments, server-based firewalls can be used for the general reason of blocking web-based access to certain websites like Facebook, YouTube, and the kinky types of sites that are unacceptable and untrusted to be accessed while the user is logged into the corporate network.
On the external side of the corporate network, server-based firewalls would likewise block any external/rogue computers found outside the IP range of the corporate network from accessing the internal corporate resources.
Overall, hardware firewalls can be essential for a corporate environment; but, it does require expert knowledge to setup each advanced configuration within the firewall and can be a down right pain to reconfigure when there is a change in the network that can make configuration again difficult to be done to get the firewall to run properly.